

July 2014: Don’t let a scammer scare you into believing your computer is infected with a virus or is sending them error messages. Even if the caller claims to be a representative from Microsoft or another genuine service provider, you should be very wary of anyone who calls you out of the blue and tries to trick you into letting them gain remote access to your computer.
SCAMwatch has heard several variations of this scam, but generally the caller will claim they suspect your computer is infected and that they need remote access to check. If you allow them access, they will then pretend to run a scan and report that your computer is infected. The caller will then try to convince you to purchase anti-virus software straight away to remove the infection. The fee may be a one-off payment or an ongoing subscription.
There are many potential dangers. As well as losing money to the scammer by paying for a service that provides you no benefits, your personal and banking details are also at risk. If you give a scammer remote access to your computer, they can cause all sorts of mischief – including infecting your computer and acquiring your personal information.
If you receive a call like this, just hang up.
Protect yourself
A variant of ransomware making the rounds aims to leverage the public’s increasing concern with regard to the NSA’s recently declassified PRISM surveillance program. Upon infection, the ransomware will lock down a computer’s web browser and display a warning message claiming illegal content was found on the machine.
As with other ransomware, users are advised that they could face anywhere between six months to 10 years behind bars and a fine of up to $250,000 unless they pay a small fee of just $300 using MoneyPak. The latter option will classify the incident as occasional or unmotivated and they are off the hook.
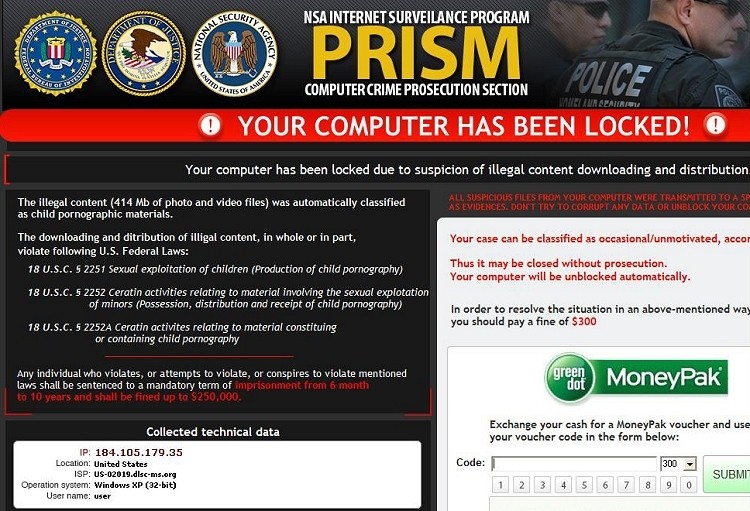
As you can see from the screenshot above, the warning is plastered with ominous seals from the FBI, the Department of Justice and the NSA – oh and there’s even an image of police officers thrown in for good measure. Collected technical data like the user’s IP address, location, ISP and operating system are also included to beef up the warning’s legitimacy.
Naturally, we wouldn’t expect any of our readers to fall for this type of scam but those with little knowledge about computers or individuals that might have heard about the NSA or PRISM could easily fall victim. Of course, the fact that several of the words in the warning are misspelled combined with the idea that a federal agency would let someone buy their way out of such a crime should be enough to raise some red flags even for those that know very little about computers.
Reprinted from Tech Spot : http://www.techspot.com/news/54085-nsa-themed-ransomware-leverages-public-concern-over-privacy.html

|
 Don't be fooled by this tempting offer -- it's most likely a scam.
Don't be fooled by this tempting offer -- it's most likely a scam.
CREDIT: Sophos Security |
Who can resist a Costco gift card? I mean, they sell cereal in bulk.
But if you see a Facebook ad claiming that you can "Get a Free $500 Costco Gift Card," you're going to have to be strong and resist.
There is no $500 Costco Gift Voucher. This is just a scam intended to get users to click through to potentially malicious websites.
Many companies use Facebook to promote their products. It's not uncommon for them to ask users to like their pages or share their posts in order to get a promotion
For more on this click here ! Reprinted from Tech News DAily.
If you want to panic over a mysterious transaction on Ebay to the tune of $564.48 for a “Microsoft Windows 8 Pro Anytime Upgrade”, then this is probably the email you’ve been waiting for.
It reads:
You have made an Ebay.com purchase.
Hello [removed],
You sent a payment of $564.48 USD to [removed].
Microsoft Windows 8 Pro Anytime Upgrade
Item# 16 $564.48 USD
Click to Enlarge
Clicking the link in the fake PayPal email will take end-users to the usual round of Cridex / Blackhole URLs. On a similar note, there’s an additional email floating around that claims you purchased 84 copies of “Vintage photo collection sexy college girls 1990s or 2000s”.
Click to Enlarge
Last time we saw this one was back in June where the tally was 23, so I guess the book is really popular. As above, Cridex is the name of the game so be sure to only check anything you’ve ordered by logging into your chosen service (and to be fair, you should have a pretty good idea of whether or not you ordered 84 copies of a “sexy college girls” book).
Christopher Boyd reprinted from GFI Labs
There may only be 26 days until Christmas, but you can get your hands on a jolly bundle of “My computer is on fire and would you like a mince pie” considerably faster than that.
Here’s a rather seasonal looking fake UPS delivery notification, claiming in broken English that “Your package delivered to the nearest Postal Office. When receiving, please show a mailing receipt. Address of the nearest office you can find on our website”.
Click to Enlarge
Depending on the spam campaign you happen to stumble upon, you’ll most likely be redirected through a collection of websites before arriving at your final destination which in this case happens to be Fake AV – specifically, System Progressive Protection.
Click to Enlarge
Fake UPS spam is a perennial favourite of Malware pushers, but this is certainly the most festive one we’ve seen so far. We detect the above as Lookslike.Win32.Winwebsec.p (v), and I’ll embrace my Master of the Obvious crown with relish as I advise anybody reading this to treat delivery notification emails with the utmost caution. If in doubt, simply visit the website of your chosen parcel delivery service and have fun typing in tracking codes instead. It’s a lot safer.
Christopher Boyd (Thanks to the Labs for finding this)
 For years, we’ve seen reports about criminals preying on internet users
using prefabricated email appearing to originate from legitimate e-card
companies. Criminals had used the brands of
Regards.Com,
AmericanGreetings.Com,
GreetingCards.Com, and
Hallmark.Com, just to name a few, on their campaigns.
For years, we’ve seen reports about criminals preying on internet users
using prefabricated email appearing to originate from legitimate e-card
companies. Criminals had used the brands of
Regards.Com,
AmericanGreetings.Com,
GreetingCards.Com, and
Hallmark.Com, just to name a few, on their campaigns.
Malicious e-card spam—the kind that leads users to download malware or phishing sites—is in the news lately. Usually, these campaigns pop up and peak whenever holidays like Easter and special occasions like Valentine’s Day are approaching.
However, there are also e-card campaigns that just randomly arrive in user inboxes unbranded. Regardless of whether these campaigns appear to have been sent by spoofed accounts or by people you actually know (whose accounts were probably compromised), the emails usually look simple, graphics-free, but overall spammy and, therefore, must be treated with enmity—i.e. Bin it!
In a recent find by one of our research engineers in the AV Lab, this e-card spam campaign not only came out of nowhere, it also carries the 123Greetings.Com brand and resembles the simple, graphics-free look of its legitimate email notification.
click to enlarge
From: 123Greetings.com
Subject: You have received a Greeting ecard from 123Greetings.com
Message body:
You have received a Greeting ecard from 123Greetings.comYou can download and view it by clicking here:
www(dot)123greetings(dot)com/(space)send/view/063071117097147476Using our new tracking feature, you can now view all the ecards received by you in the last 30 days. Your ecard is going to be with us for the next 30 days.
Based on user feedback, 123Greetings.com has launched 6 new pages with the best ecards in the Most Popular/ Most Viewed/ Highest Rated/ Latest Additions/ Popular Now and Always There Sections listed on the homepage. So hurry up and choose the best ones for sending them from the links below:
< links that lead to actual pages within the 123Greetings.Com domain >
Clicking www(dot)123greetings(dot)com/(space)send/view/063071117097147476 leads users to download the malicious file, card.exe. Running this executable file enables it to drop server.exe. server.exe is a backdoor program that, in turn, drops two copies of itself on systems—svchost.exe and services.exe: files that use actual names of Windows files—and connects to a PHP file hosted on a legitimate but possibly compromised news website in the Middle East. The said executable connects to this file in order to download more files or update itself and its copies.
The Labs has reason to believe that the spammer behind this particular e-card uses Umbra Loader, a popular do-it-yourself (DIY) botnet building tool, to distribute malware.
Our friends at Webroot published a preview of the said tool not so long ago.
GFI VIPRE Antivirus detects card.exe as Trojan-Downloader.Win32.Umbald and the backdoor executable files as Backdoor.Agobot (fs). If you recall, the Agobot malware is capable of exploiting software vulnerabilities on affected systems.
So, dear Reader, in case you see this particular 123Greetings.Com email in your inbox, don’t just frown upon it. Bin it.
Jovi Umawing (Thanks to Patrick for spotting this) reprinted from GFI Labs
The Internet is a fascinating place, isn’t it? For me
it’s a combination world’s fair, library, amusement park and shopping mall all
rolled into one. The ability to transport oneself at the click of the mouse
is simply an incredible experience. But there are dangers in that fascination.
Like anyplace you might go these days, whether in the big city or out in the
country, there are criminals, thugs, gangs and pickpockets. So you need to watch
your step, pay attention to what you’re doing and not end up a victim. One thing
you especially need to watch out for is your own itchy clicker (trigger) finger.
There are so many come-ons, especially on sites like Facebook; you’re faced
daily with a barraging myriad of goodies. Some even look too good to be true,
like getting that iPad for 20 bucks (it is too good to be true). You need to
think before you click no matter how dazzling the “gimmees” are – free gift
cards (yeah right) and downloads of newly released movies (no way) are just
part of the promised bounty.
And look out for friends bearing gifts or recommendations.
Sometimes what looks like an endorsement from a pal is just another criminal
wearing your friend’s ID. Twitter, Pinterest, Facebook, et al. are ripe grounds
for the bad guy, so you really have to pay attention. Think before you click.
You’ll prevent endless hours of anguish and potential harm to your files and
computer. You might even have to be a bit antisocial with your social media
– just be smart. Your best suit of armor when visiting your favorite places
is your security software, so keep it up to date! And if you get this sudden
urge to discover who is accessing your profile – DON’T DO IT!
Phone and support scams
There has been an increase in “Microsoft” support
calls lately. If someone calls you stating they are from Microsoft, chances
are pretty darn good that they aren’t and that they just want to get into your
computer and do nasty things. These are actual phone calls, so don’t be surprised
if you should get a call one morning with some cybercriminal knocking at your
firewall to be let into your domain. We have heard of some instances of where
there have been VIPRE support calls being made. We have also seen a couple of
websites stating they do VIPRE support. Only get the real thing from us. GFI/VIPRE
is the only valid resource for your support problems. Here’s some
important information from Microsoft on
these supposed calls.
Gone phishing for PayPal
We’ve seen a recent influx of PayPal phishing attempts,
where the user is instructed to confirm their account information and if they
don’t, the account will be “suspended.” Emails are coming from service@paypal-team.com,
for example, with the subject line, “Your account has been limited until we
hear from you!” Don’t fall for these scams and contact PayPal immediately if
you receive such an email.
Octoshape safe?
Reader Steve asked, “I downloaded Octoshape for live
streaming video. I have read some reviews that suggest Octoshape allows intruders
easier access to my computer. Can you comment?”
I checked with our Security Product Manager, Eric Howes,
and he provided the following response:
“Octoshape is a P2P media player web browser plugin.
At present I know of no exploits for Octoshape, which is not to say that there
couldn’t be one in the future. The big problem with Octoshape has always been
poor notice/disclosure of its P2P functionality at install time. This thing
first popped onto our radar screens when CNN installed it onto the PCs of visitors
in January 2009 trying to watch a live stream of President Obama’s inauguration.
The install generated a lot of complaints when users learned of the P2P technology
at the core of the app, which uses P2P connectivity to maintain a healthy bitstream
for all viewers of a feed.”
Sue to the rescue
Apparently we’ve trained reader Sue very well! She wrote
in to say, “I enjoy reading the newsletter. Over the last six months, I’ve received
three emails from people I know that were ‘stuck in a foreign country and needed
money wired to them.’ These people were in three separate groups I’m involved
in. As I know their email was hacked and it was a scam, I immediately turned
around an email to everybody in that circle that I had email addresses for,
with a title warning people that it was a scam and not to send money. It was
really scary to get emails on two of the three occasions from people that were
preparing to wire money, but didn’t because of my email.”
Best,
Larry Jaffe
Editor, VIPRE Security News
About GFI Labs
GFI Labs specializes in the discovery and analysis of dangerous vulnerabilities
and malware. The team of dedicated security specialists actively researches
new malware outbreaks, creating new threat definitions on a constant basis for
the VIPRE home and
business antivirus
products.
About GFI
GFI Software provides web and mail security, archiving and fax, networking and
security software and hosted IT solutions for small to medium-sized businesses
(SMB) via an extensive global partner community. GFI products are available
either as on-premise solutions, in the cloud or as a hybrid of both delivery
models. With award-winning technology, a competitive pricing strategy, and a
strong focus on the unique requirements of SMBs, GFI satisfies the IT needs
of organizations on a global scale. The company has offices in the United States,
UK, Austria, Australia, Malta, Hong Kong, Philippines and Romania, which together
support hundreds of thousands of installations worldwide. GFI is a channel-focused
company with thousands of partners throughout the world and is also a Microsoft
Gold ISV Partner.
Disclaimer: All product and company names herein may be trademarks of their
respective owners. To the best of our knowledge, all details were correct at
the time of publishing; this information is subject to change without notice.
 |
JFD is now offering the classes needed to upgrade your pistol license in NY from target hunting to a full carry . The
Class schedule is posted under the CCW class button to the left. For
information Call or text Pat at 516-313-4355 or Mike at 516-265-6816 To request a class application email CCWClass@jfd-ltd.com
The next class Will be on June 2024 8th and 9th. Weekday classes are available. For aditional information call or text the number above!
New Profile Spy Spam Spreading on Facebook Leads users to a survey scam
A new Facebook scam lures users into signing up for premium mobile services
and spamming their friends by promising to show a list of profile visitors.
It even instructs users to disable ad-blocking programs. Read the full article
:
http://www.sunbeltsecuritynews.com/QU57EP/100811-Facebook-Spy-Spam
How Does a Computer Get Infected with Rogue Antivirus Programs?
The reason these rogue anti-virus programs are successful (for the malicious coders) is because the warning screens very closely resemble legitimate Windows warning screens, plus the rouge software program names closely resemble or sound like legitimate antivirus programs. When you load an infected Web site you might see a warning screen pop up and think that it is a legitimate Windows warning. Users unknowingly are tricked into downloading the software because they believe the warning to be a legitimate Windows messages. You might also be on a Web site trying to view a video and a screen may pop-up telling you that you need to download a codec to view the file. The window prompting you to download the codec looks legitimate, however you are not going to download a codec—instead you will receive one of the many rogue antivirus software programs. In April of this year, it was also reported that systems that had been previously infected with Conficker, found this worm had began installing rogue antivirus programs on infected machines. In the early cases this turned out to be a rogue application called SpywareProtect2009. Kaspersky researchers reported this was a typical rogue program that offered to clean the computer for $49.95. Lastly, if you use file sharing networks you also risk downloading a rogue antivirus as it can be easily hidden inside a legitimate program—that you may or may not be legitimately downloading. For more information on Rouge A/V programs see the full article hereBogus UPS shipping spam
By John E. Dunn | Techworld
Published: 16:05 GMT, 12 April 10
A new wave of bogus UPS shipping spam is being used to push a piece of malware which can render PCs unbootable, security company Webroot has warned. Read full article here,,
Hey Guys! With all the problems in Washington on Wall street and in the banking sector, more and more phishing scams are on the way! If you get an email from your bank asking you to update your personal info THINK TWICE or even 5 Times..Most banks will not ask for personal info by sending an email it may be or more than likely is someone trying to STEAL your personal info.. PLEASE if you even are slightly afraid or suspicious, CALL the BANK and ask .. (Don't call the number in the email Look it up your self )
Just remember the motto of that great bank " The First Presbyterian Bank of Scotland"; " We cannot save your soul ..But we can save your Money!"
As always be careful opening those junk attachments.
Remember.. Grandpa said" there is no such thing as a free lunch". Everybody wants something...
Safe Computing .. Pat F..
How Not to Get Infected
Obviously, there are many ways to pick up a virus or other malicious software.
We've put together a list of the more common methods of infection so that
you know what to look out for and avoid.
10 email scams to watch out for (click here)
If you are using WordPress, Opera or Firefox, make sure you get your
updates.
FAKE Microsoft OUTLOOK Update!!
A fake E-mail notifying of a Microsoft outlook/outlook express Update is going around.
Microsoft DOES NOT send out e-mail notifications of patches/updates. This is malicious software contained in the link . Here is an article about the potential threat. Fake Microsoft patches themed malware campaigns spreading | Zero Day | ZDNet.com.
Remember follow safe computer practices and watch what you download and open in E-mails ....even from senders your know.
Google Sponsored Links Spreading Rogue Anti-Virus Software
sunbeltsecuritynews.com